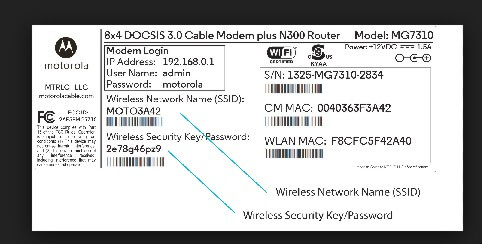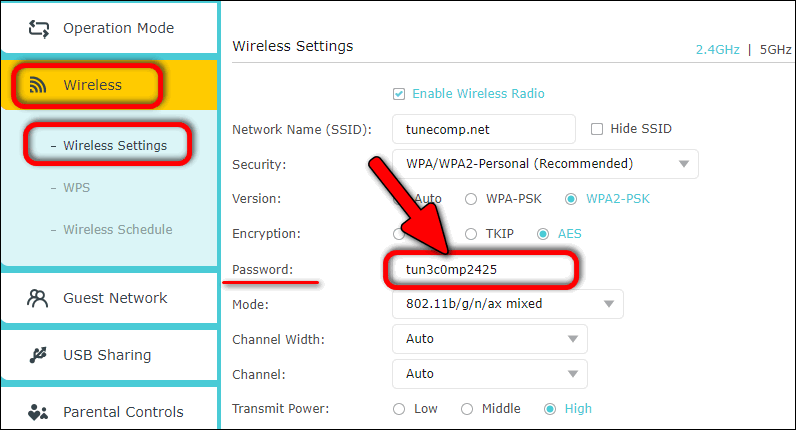
What is Network Security?
- 0
Listed below are three key types of network security: Firewalls, Intrusion prevention systems, and Network access control. To get a full understanding of each type, read on. Before you choose which type is best for your business, you should be aware of what all devices are connected to the network. There are various types of malware that can infect your network. To protect your business, be sure to install firewalls on all devices and update your network software to protect your systems.
Firewalls
Firewalls are part of network security because they can protect your network from malicious attacks. These devices are used by companies and consumers alike. Today, modern organizations incorporate firewalls into their SIEM strategy. Firewalls can be installed at the network perimeter or within the network, creating segmentation to protect against insider threats. Firewalls perform important logging functions and keep records of events. The rules for a firewall should be updated regularly, as vendors find new threats and develop patches for them.
One type of firewall is stateful inspection. It checks for functional packets that belong to an existing connection and allows or blocks them. This kind of firewall is similar to proxy firewalls. However, it is important to know that stateful inspection firewalls are not as secure as stateful inspection firewalls. These firewalls are vulnerable to attacks that exploit established connections. If you are concerned about this kind of security, you can use a reverse proxy firewall.
Intrusion prevention system
An intrusion prevention system (IPS) is a type of network security solution that uses sophisticated technology to detect and prevent network attacks. It reduces security incidents by limiting the traffic that reaches other security controls, including firewalls. Because it detects malicious traffic in real-time, it also minimizes security alerts and network disruption. Unlike firewalls, which store content, IPS only records network activity when it takes action. Instead, it subscribes to a reputation-based list of malicious sites and domains.
Today’s IPS solutions are capable of stopping denial-of-service attacks, brute-force attacks, and other malicious activities. They can even protect against vulnerabilities, such as those found in popular spear-phishing vehicles. IPS technologies use advanced features, such as real-time deep packet inspection to identify threats. They can also deny use of insecure protocols and monitor internal compliance to protect a company’s network.
Network access control
Network access control (NAC) is a technology that controls network activity and restricts network resources to only those devices that comply with security policies. NAC allows administrators to monitor network activity and mitigate the risk of network attacks by blocking non-compliant devices, isolating them, and automatically fixing them without the attention of network administrators. It also allows organizations to set up different network segments, called subnets, which separate and connect different network resources using IP addresses. NAC has been around since the early 2000s, but its features have become more sophisticated with changing technologies.
Increasing security is more important than ever. Network access control helps organizations limit the scope of malicious behavior. Researchers estimate that 360,000 malicious files are downloaded by employees every day. Without proper access control, authorized users can accidentally turn a device rogue and spread the malicious file across the network. Network access control also helps prevent unauthorized use of sensitive data and intellectual property. In addition, network access control limits the risks of accidental data theft and data loss by limiting access to a subset of employees or users.